- How much do employees actually know about cybersecurity?
- What initiatives have companies taken?
- Confidence vs. knowledge — how protected do employees feel?
- Enforcing good habits — easier said than done
- Office vs. remote working — different environments produce different habits
- How can companies better protect themselves?
- Conclusion: Training is the first line of defense
They say crime doesn’t pay. But when we’re talking about cybercrime, the numbers tell a different story. Damages relating to cybercrime are expected to reach a value of $6 trillion in 2021 alone. And with the rise of remote work due to the COVID-19 pandemic, companies are in hackers’ crosshairs more than ever before.
Ninety percent of companies faced an increase in cyberattacks due to the pandemic, according to a survey of 1,000 CXO’s conducted in June 2020. Even more alarmingly, 93% of these CXO’s said they were forced to delay security projects in order to help manage their company’s transition to remote work.
TalentLMS partnered with Kenna Security, an industry-leading penetration testing and vulnerability management firm, to survey 1,200 employees on their cybersecurity habits, knowledge of best practices, and ability to recognize security threats. Here are some of the staggering results that offer some explanation as to why cybercrime has grown into such a lucrative business:
- 69% of respondents have received cybersecurity training from their employers, and yet, when we asked them
to take a basic quiz, 61% failed - Only 17% of surveyed employees working in information services passed the quiz, compared to 57% of healthcare
employees - 59% of employees received cybersecurity training in response to the rise in remote work as a result of the COVID-19
pandemic - 60% of employees who failed our cybersecurity quiz report that they feel safe from threats
- More employees store their passwords in plaintext than those that keep them in password managers
- Office employees report feeling safer from cybersecurity threats than remote ones, but have much worse security habits
- Experts offer advice on how to improve cybersecurity training initiatives for better results
How much do employees actually know about cybersecurity?
Let’s face it — learning about cybersecurity probably isn’t a top priority for the average employee, especially if they’ve never been the victim of an attack (that they know of). Most employees who work in offices or remotely use a computer to do the majority of their work. But how much do they know about strong passwords, malware, phishing attempts, and more?
With the help of top security experts from TalentLMS and Kenna Security, we designed a seven-question quiz to discover just how much employees do or don’t know about fundamental cybersecurity principles. Respondents ranged from 18–54+ in age, and work in a variety of industries in the U.S. They all use a computer to do most of their work, with 43% working from an office, and 57% working remotely. Respondents who answered four or more questions correctly were considered as having passed the quiz, while those who got three or less correct failed.
Based on this scoring system, 60% of respondents failed the assessment. In fact, 7% of respondents answered every single question incorrectly, while less than 1% of respondents got all seven questions correct.
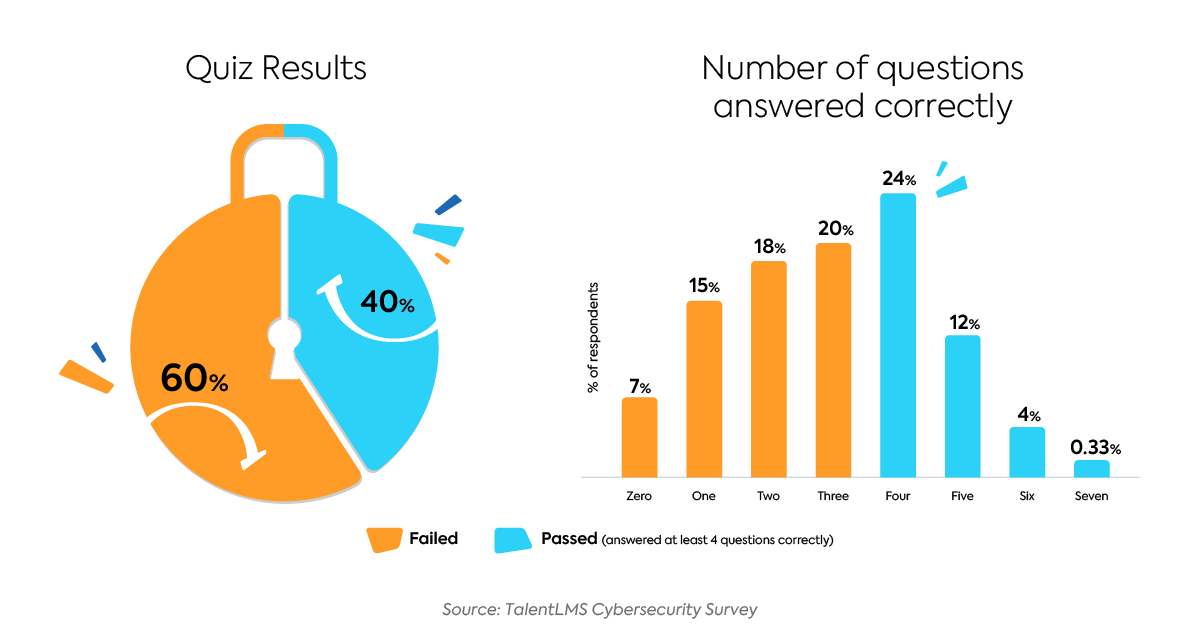
You might be thinking, “But that’s not fair! If an employee has never been taught about cybersecurity risks and best practices, then they can’t be expected to know the answers.”
Except 69% of all respondents have received cybersecurity training from their current employers (yes, we asked). And strangely enough, these employees’ quiz results were slightly worse than those of the employees who report not having received cybersecurity training from their employers.
Of the respondents who have received training, 61% answered fewer than four questions correctly. And out of all the respondents who answered all seven questions wrong, 80% reported having received training.
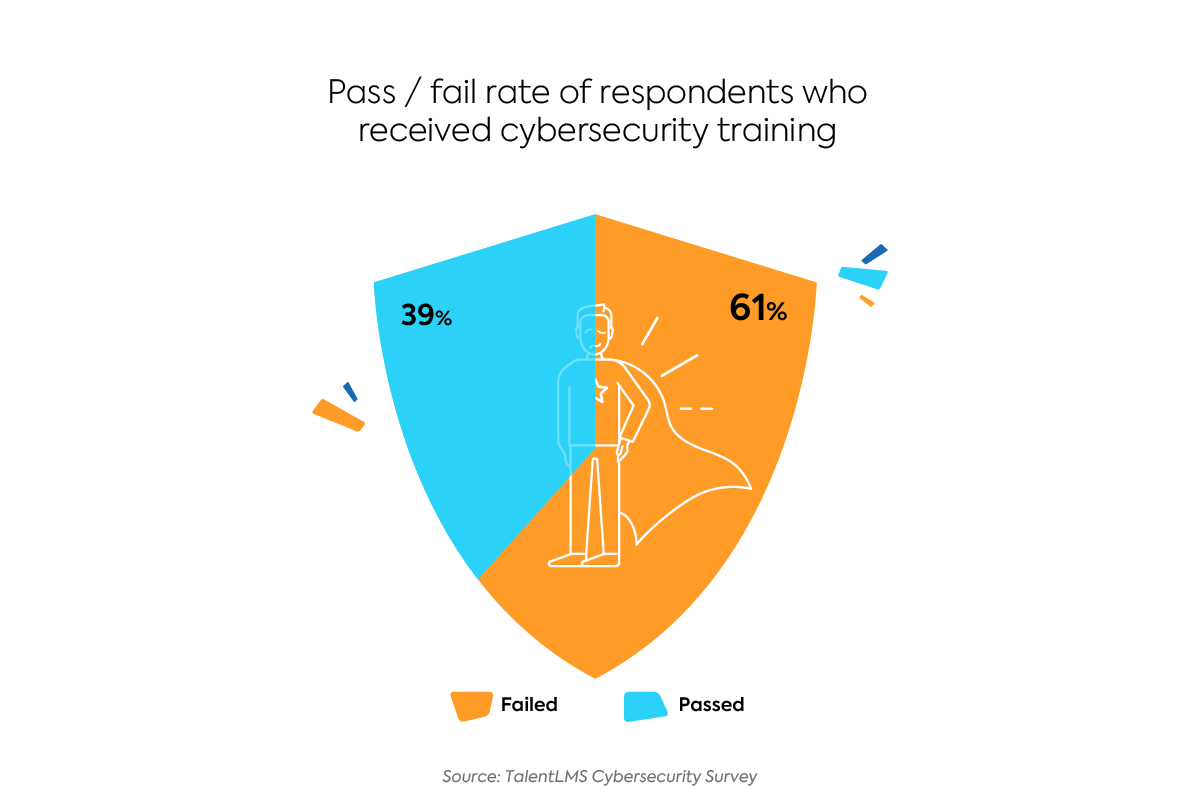
These staggering results lead to the conclusion that simply having a cybersecurity training program in place isn’t enough. (Read more about achieving better results through effective cybersecurity training below).
Despite their largely inherent familiarity with technology, employees aged 18-24 collectively performed the worst on the quiz, with only 16% of them passing. Twenty-five to 34-year-old’s tied with those aged 54 and over for the best collective performance, with a pass rate of 43%.
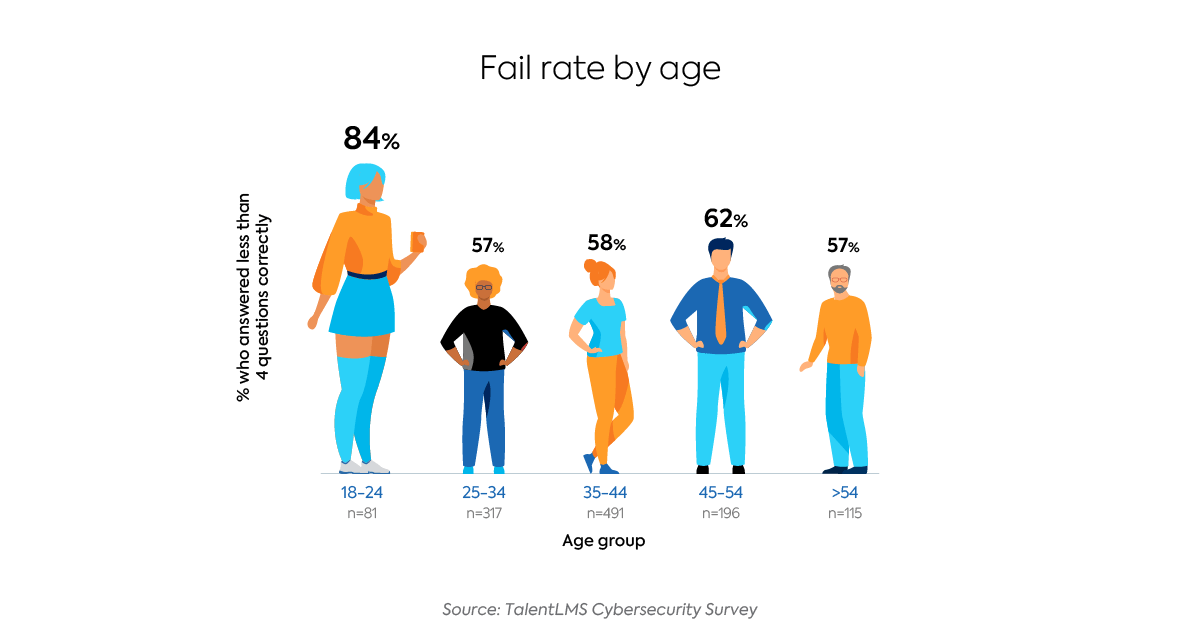
It would be reasonable to expect that employees working in certain industries would have more knowledge about cybersecurity than those in seemingly unrelated industries. For example, you’d expect professionals working in information services and data to perform better on the quiz than professionals working in healthcare and social assistance.
But only 17% of employees in information services passed the quiz, compared to 57% of healthcare employees. As a matter of fact, employees in the former group collectively performed worse on the quiz than any of the other main industries respondents were employed in.
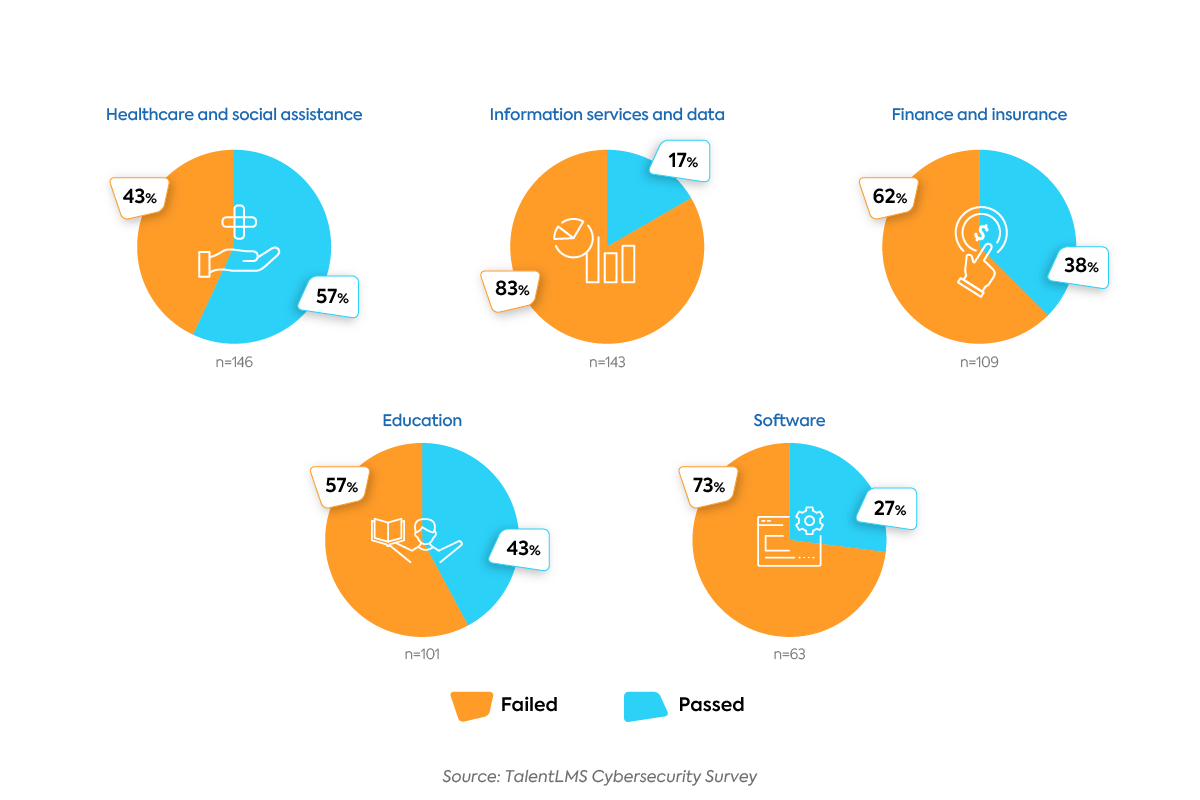
And yet, 93% of respondents working in information services report receiving cybersecurity training, compared to 67% of healthcare respondents. While all of these employees do the majority of their work from a computer, it’s clear that their knowledge of cybersecurity varies drastically across industries.
By now you might be wondering, “how hard was this quiz?” Check out the exact questions we asked our respondents, as well as the correct response rate for each:
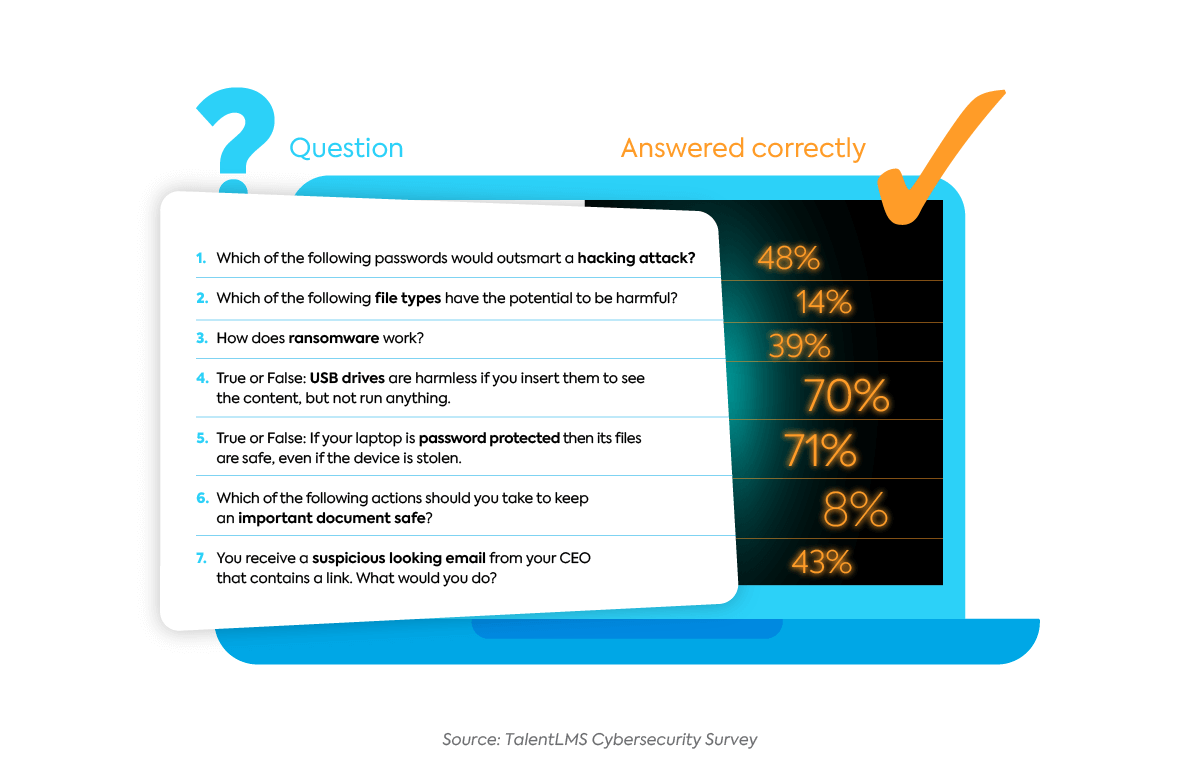
The numbers show that employees were most knowledgeable in laptop security. On the other hand, they were least knowledgeable in securing documents with sensitive information, and recognizing harmful file types.
Overall, these quiz results show that the average employee’s knowledge of cybersecurity threats and best practices is limited. And while most employers are providing their people with some kind of training on the topic, it’s not hitting the mark, and has a poor return on investment.
What initiatives have companies taken?
While protecting themselves from cybersecurity threats and attacks has been a long-standing priority for companies, the COVID-19 pandemic further solidified this need as much of the world transitioned to working remotely. With a massive boost in online work also came ample opportunity for hackers to exploit any weaknesses in employees’ systems and communications. And they did.
According to a recent report by Deloitte, more than 500,000 people worldwide were affected by cyberattacks on video conferencing services between February and May of 2020. These hackers stole and sold personal data on the dark web that they had intercepted from video calls.
Most companies are at least aware of the increased threat brought on by remote work and have attempted to respond to it.

The majority of employees also report that their companies have implemented the correct fundamental safeguards that provide essential protection from cybersecurity threats:
- 66% require employees to use 2-factor authentication
- 67% have an established policy for reporting lost and stolen devices
- 75% enforce mandatory periodic password changes
Despite these numbers, it’s no secret that determined hackers are way ahead of the protections that companies have put into place, and there’s a lot of catching up to do.
“These survey results show that while most of the employees surveyed show that their companies are moving in the right direction, there is a large number of companies that are not providing basic cybersecurity training (31%) or offering multi-factor authentication for their systems (between 18 – 34%). These gaps in basic cybersecurity hygiene are what attackers often exploit and are a good reminder we still have a lot of work to do.”
Jerry Gamblin
Director of Security Research, Kenna Security
Confidence vs. knowledge — how protected do employees feel?
Whether or not employees follow best practices and exhibit safe behaviors directly depends on if they feel the need to.
When we asked all respondents if they feel safe from cybersecurity threats, 56% responded “yes,” 25% “no,” and 19% “unsure.” The numbers skew even further when we look at the responses of employees who failed the quiz.
Sixty percent of people who answered less than four questions correctly answered “yes” to feeling safe from threats. Forty-nine percent of those who passed said the same.
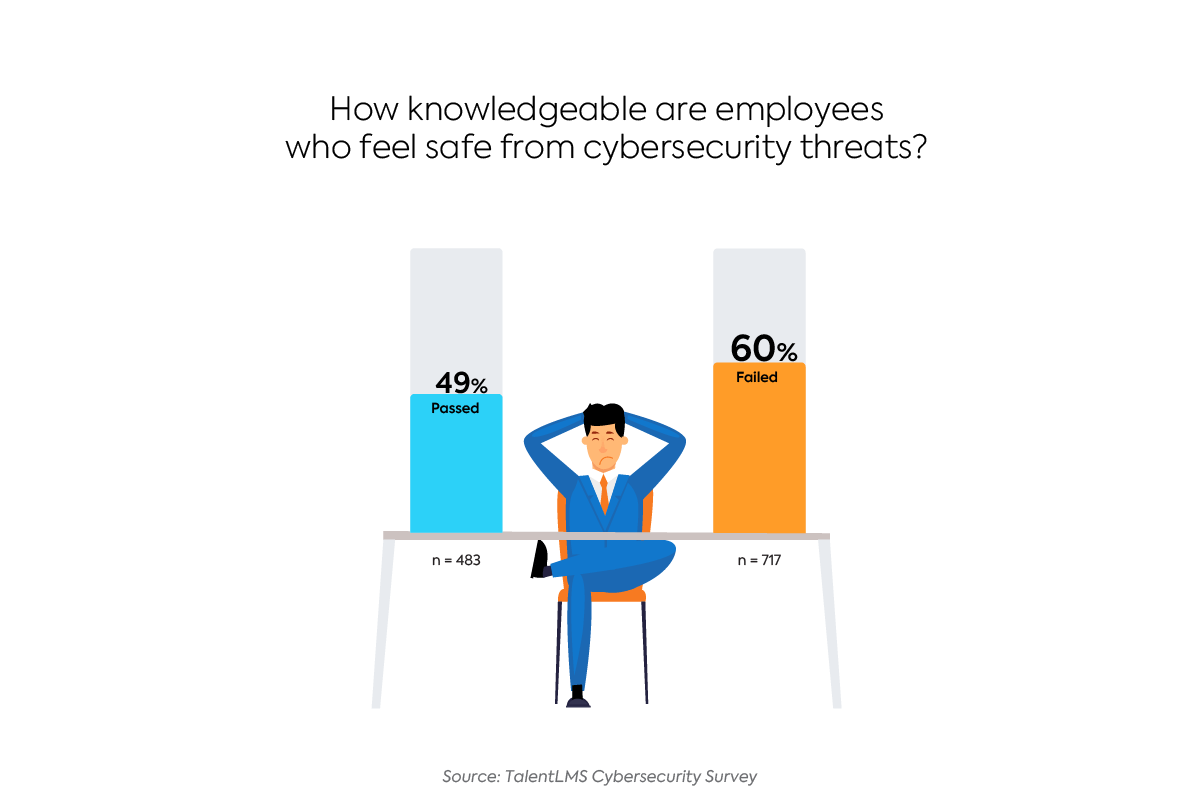
This phenomenon is known as the Dunning-Kruger effect. The theory states that people with very limited, or no knowledge on a particular topic tend to overestimate their ability in that area, and feel more confident than they reasonably should. As we gain knowledge in a particular field, we become more aware of all the things we don’t actually know, and our confidence quickly declines.
This reasoning offers an explanation as to why 74% of respondents who answered every single question incorrectly report feeling safe. Meanwhile, not one of the mere 4 of 1,200 respondents (0.33%) who got all seven questions correct said the same.
Enforcing good habits — easier said than done
Establishing company-wide policies is one thing, but actually getting people to follow them is another. The fact is that companies are only truly protected when their employees follow cybersecurity best practices. IBM’s 2014 Cybersecurity Intelligence Index found that 95% of breaches were caused by human error. A similar 2019 study conducted by CybSafe found that number to be 90% among UK cyber data breaches.
According to our survey results, 77% of employees reported that their company has an established cybersecurity policy, but 19% of them admit they’re not familiar with it.
One of the most basic ways that a company keeps its data safe is through strong and secure passwords. We asked employees where they store their passwords, and the results left much to be desired.
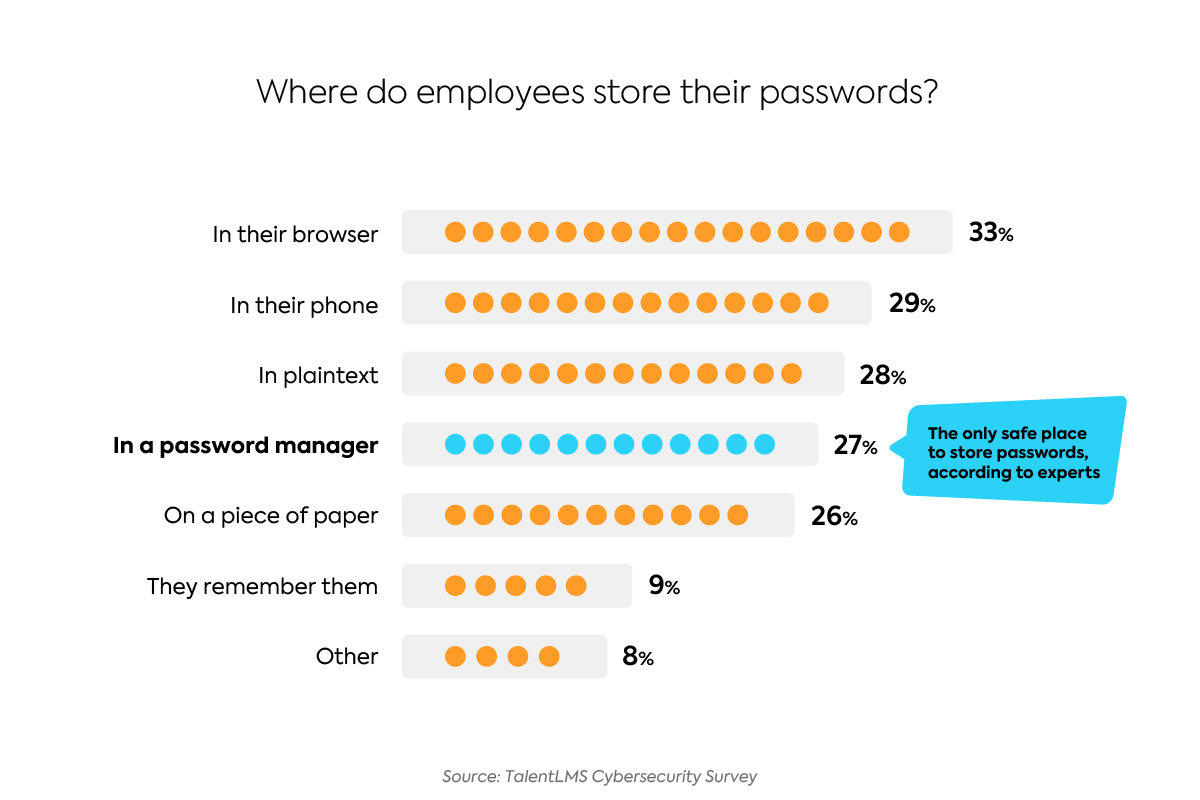
A stunning 33% of employees store their passwords in their browsers — a habit that is far riskier than most realize. Suppose an employee hasn’t set up a master password; in this case, it’s possible for anyone who has access to their computer, either physically or remotely, to open the browser and view the person’s actual passwords.
Even worse than storing passwords in the browser is storing them in plaintext, or written on paper. Storing them this way leaves them completely unprotected. Anyone could find the paper, or access the unencrypted file where they’re written, with minimal effort.
Nine percent of employees even claimed that they simply remember all of their passwords. But considering the huge number of passwords an average person has, it’s highly unlikely that they remember them all without reusing the same password for multiple accounts.
Prior to the COVID-19 pandemic, a study conducted by NordPass found that the average person has between 70-80 passwords. The company reconducted the study and revealed in October 2020 that the number is now around 100, a 25% increase.
Ideally, every password a person has should be completely unique from all their others. But it’s safe to say that this isn’t the case for at least 73% of respondents who aren’t using a password manager.
One survey respondent even specified, “I typically don’t write my passwords down. I try to keep them the same. When I have to change one, I change the rest to match.”
For these reasons, experts assert that the only right answer to where people should be storing their passwords, both work and personal, is in a password manager.
As with employee knowledge, the impact that training has on employee behaviors is mixed. Five percent of the employees who have not received training don’t use any security features to protect their work computer. That number drops down to 1% among employees who have completed training.
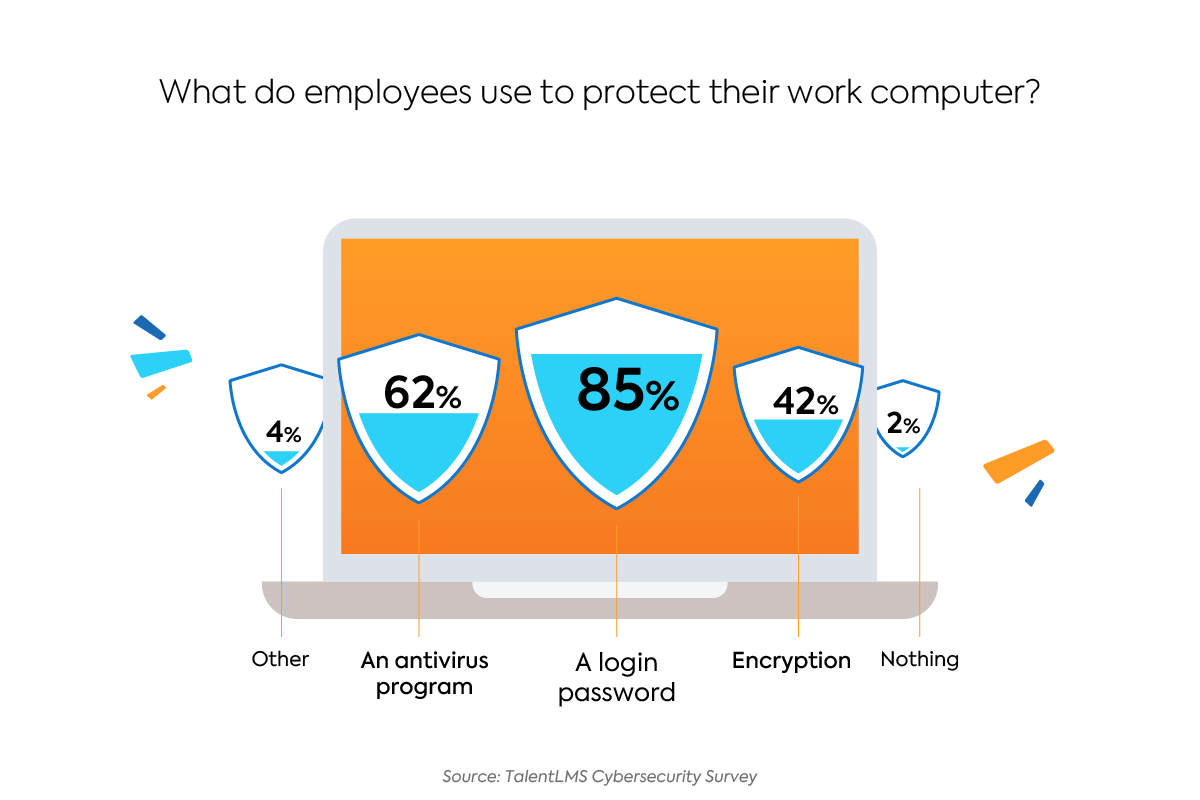
Employees with training generally exhibit better habits when it comes to protecting their computers than those that haven’t received training. Eighty-eight percent use a password, compared to 79% of those without training. Forty-eight percent use encryption, compared to 28% without training. And 29% of trained employees use a password manager, compared to 22% of those without training.
There are two notable exceptions where employees with training actually exhibit more unsafe behavior than those without:
- 34% of those with training still store their passwords in plaintext, compared to 16% of those without training
- 60% use public WiFi to work, compared to 52% of those without training
Office vs. remote working — different environments produce different habits
Remote workers have always presented a challenge to companies’ efforts to secure themselves from cybersecurity threats, and the surge in remote work due to the COVID-19 pandemic has only intensified the problem.
Cyberattacks grow more sophisticated every day, and hackers have stepped up their game, particularly over the last year. Before the COVID-19 pandemic, 20% of attacks were carried out using previously unseen malware or other methods. That number has jumped up to 35% since the start of the pandemic.
Remote employees are aware that things have changed. The survey results revealed that remote workers collectively feel less safe than office employees — but are they?
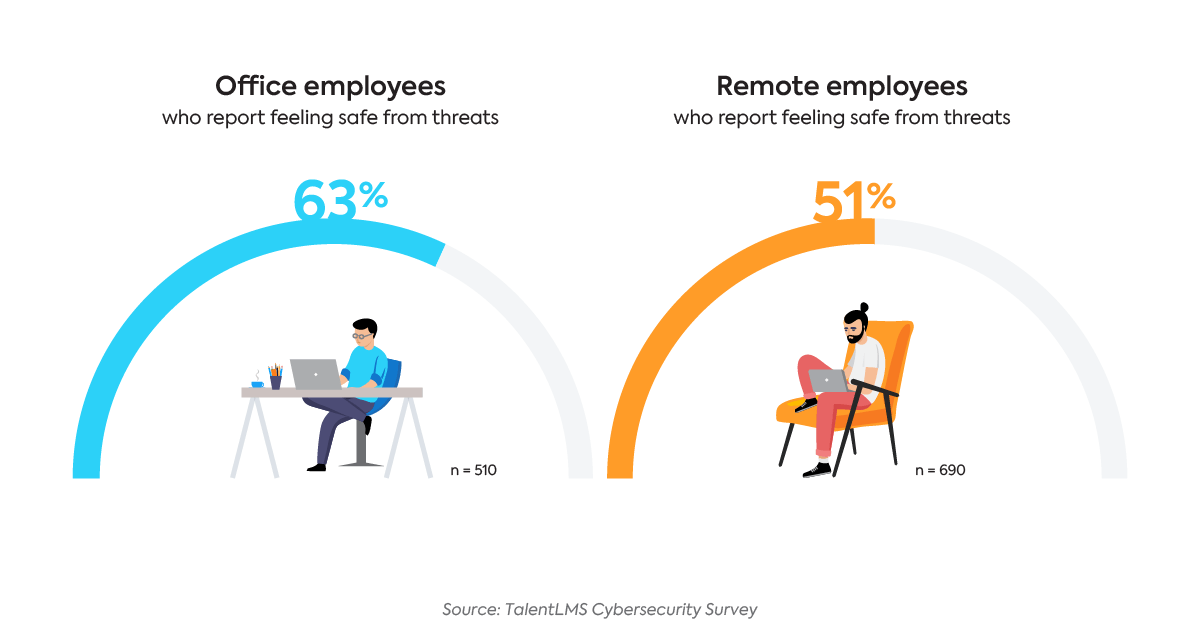
This difference in perceived safety offers a possible explanation for the fact that remote employees actually demonstrate better cybersecurity habits than their office-bound counterparts:
- 32% of remote employees use a password manager, compared to only 20% of office employees
- 49% of remote employees protect their laptops using encryption, compared to 32% of office workers
- 65% of office workers report they sometimes use their personal devices for work, compared to 49% of remote workers who said the same
- 36% of office workers store their passwords in plaintext, compared to only 22% of remote workers
The bottom line is that whether employees are working remotely, in-office, or some combination of these two, companies need to take active and pointed steps towards enforcing safe behavior to protect themselves from ever-evolving cyberattacks.
How can companies better protect themselves?
Respondents’ overall performance on the quiz was quite disheartening, with over half of them failing to answer at least four out of seven questions correctly. And while the survey results show that training does have a positive impact on some aspects of employees’ cybersecurity habits, these effects are not consistent across all areas, and there is plenty of room for improvement.
So how can companies do better?
TalentLMS’s Chief Information Security Officer, Victor Kritakis, spelled it out for us:
“Simply offering a cybersecurity training program does not guarantee, per se, a skilled or educated staff. Such programs are usually theoretical, full of technical terms, and, well, boring. Cybersecurity training should be fun, hands-on, and use real-life examples. And this is because staying safe and protected in cyberspace is a hands-on, practical skill.“
One of the quickest and simplest ways to improve training programs is to evaluate them from the learner’s perspective. The fact is that no one wants to sit through long, boring, jargon-filled training. Your program is more likely to resonate with your employees if it’s engaging, interactive, and appeals to multiple learning styles.
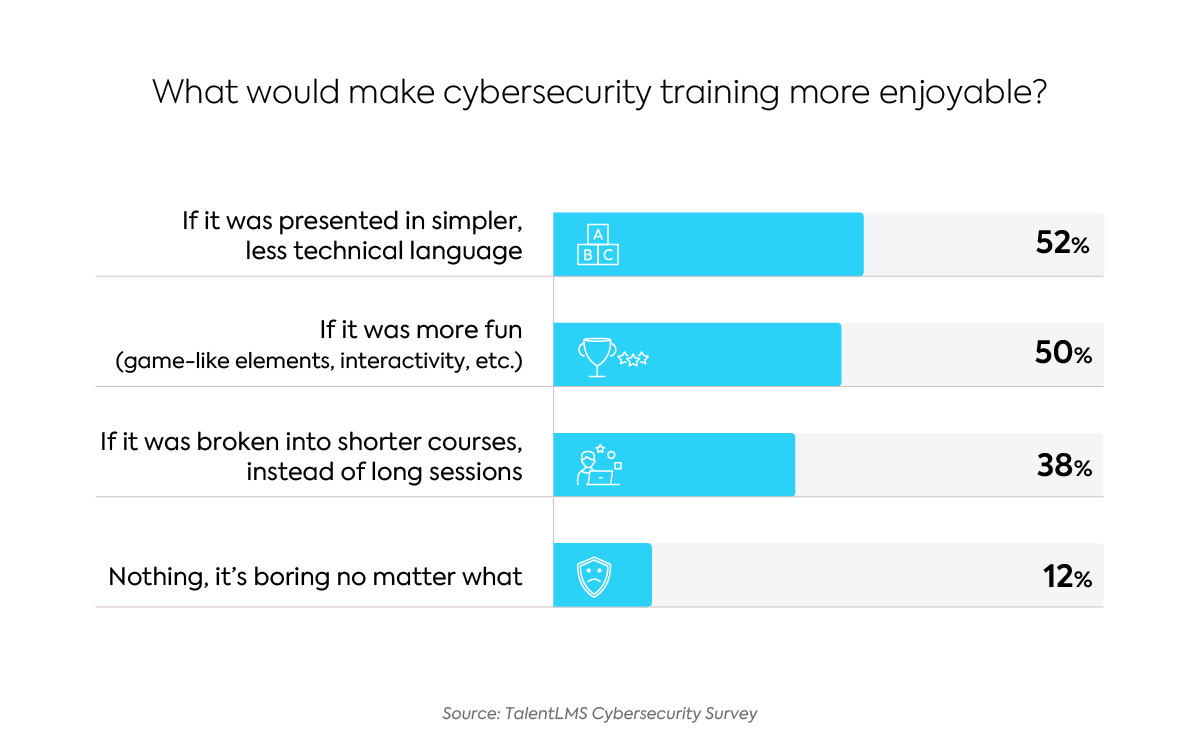
When we asked respondents what would make cybersecurity training more enjoyable, their responses were loud and clear. Training should be simpler and use less technical language, be more fun and interactive, and it should be broken down into smaller, more digestible units.
Don’t know how or where to get started on building interactive cybersecurity courses?
Look no further than TalentLibrary. Get 16 ready-made, short, animated video courses that train your people on the importance of strong passwords, the risks of ransomware, keeping data safe, and more.
“An engaging program results in more effective and adequate training for your staff, which will lead to security awareness and safe online habits.”
Victor Kritakis
CISO, TalentLMS
Conclusion: Training is the first line of defense
Whether your company has five employees, or over 5,000, cybersecurity threats are a real risk. When the vast majority of breaches are caused by human error, data shouldn’t be left out in the open to be stolen by hackers and cybercriminals. Training employees in how to spot potential threats, and to follow cybersecurity best practices, is the foundation of keeping your company and its data secure.
But while training is the answer, simply having a program in place isn’t enough. While they may be faceless, hackers and cybercriminals are real people, with expert knowledge and skills to exploit even the smallest of vulnerabilities.
That’s why to achieve real results and a significant return on your training investments, make sure your program is interactive, engaging, and designed for humans, not machines.

